Wanna try ghidra in reversing so I play Pragyan CTF.
Did not have time to solve them all.
Pragyan CTF is a much easier CTF, a good target for me to start writing my blog……
It’s a good way to force me to understand every details and improve my English writing skill (maybe).
Web
Cookie Monster
The value of flag in cookie is the md5 result of flag’s slices.
bc54f4d60f1cec0f9a6cb70e13f2127a md5 pc |
flag:pctf{c0oki3s_@re_yUm_bUt_tHEy_@ls0_r3vEaL_@_l0t}
Game of Faces
A form hidden behind the first color block, just upload any picture then you get a base64 encoded string which decoded as The_scroll_says=the_night_kingVSvalyrian.txt
Get the flag at /the_night_kingVSvalyrian.txt
flag:pctf{You_L00K_Wi3Rd_IN_H3R3}
Mandatory PHP
final solution
http://159.89.166.12:14000/?val2=WoAHh%2525252525252525252521&val1=rUs&val3=12&val4=16
detail
$a=hash("sha256",$a); |
Find a string which’s sha256 result’s prefix is 1e, so that it would be consider as scientific notation at first line. When $a='rUs', the result of sha256 is 1e40afafd2290d3f1e0cbc86cd9bbec0df8627b32730ea72e0dce67fe49a2f30, would be consider as $10^{40}$ at second line and the last result is 400, which is $12^2+16^2$, done.
next check:
for($i=1;$i<=10;$i++){ |
It apply urldecode 10 times on $b, so we have to encode WoAHh! 10 times, also. The result should be WoAHh%25252525252525252521. But,the url would be decoded once by default, we have to do one more encode, which would be WoAHh%252525252525252525252521
flag:pctf{b3_c4r3fu1_w1th_pHp_f31145}
Forensics
Welcome
binwalk -e welcome.jpeg |
The password for a.zip is in the secret.bmp, dGhlIHBhc3N3b3JkIGlzOiBoMzExMF90aDNyMyE==, decoded as the password is: h3110_th3r3!
Then it give us a a.png, the flag is hidden in the white background
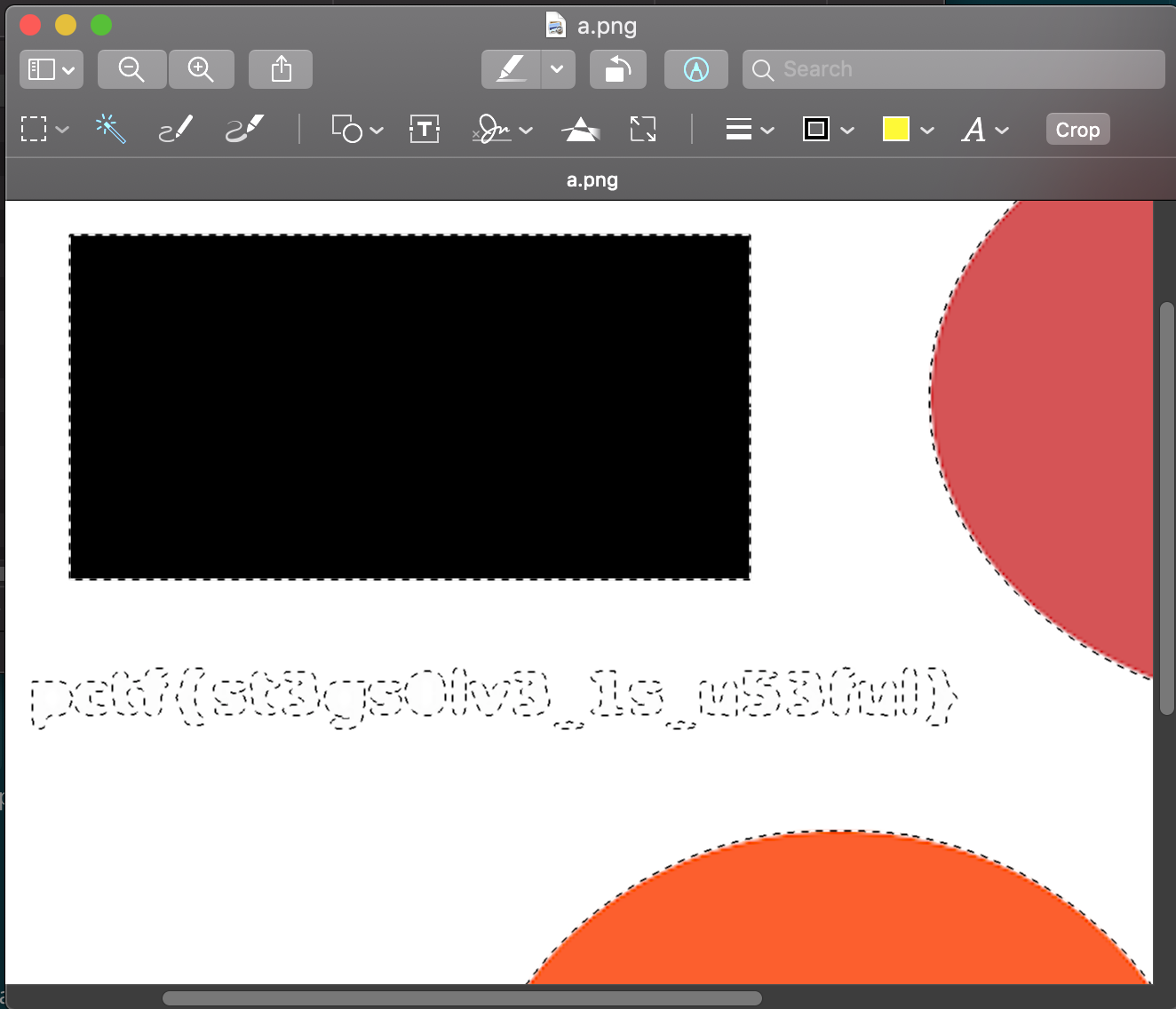
flag:pctf{st3gs0lv3_1s_u53ful}
Magic PNGs
you_cant_see_me.png is a broken png, fix it to get the password for tryme.zip
First, fix the header , the header should be 8950 4e47 1d0a 1a0a instead of 8950 4e47 2e0a 2e0a.Next, find ascii string idat in png , this is the name of IDAT chunk, the string should be uppercase. Finally, fix two CRC checksums. then we get a picture of mask from movie V for Vendetta.

According to the hint, the password for tryme.zip should be MD5 ("h4CK3RM4n") = 2c919f82ee2ed6985d5c5e275d67e4f8
flag:pctf{y0u_s33_m33_n0w!}
Save Earth
Some usb packages, extract the Leftover Capture Data bytshark -r ./SaveEarth.pcap -T fields -e usb.capdata > leftover.txt
It doesn’t look like some keyboard strike or mouse position, but more like morse code.
01:02:00:00:00:00:00:00 |
Get morse code
$ cut -d ':' -f 2 leftover.txt | sed -e "s/01/ /g" -e 's/02/-/g' -e 's/04/./g' | tr -d '\n' |
-.-. - ..-. ... ....- ...- ...-- -> CTFS4V3
flag is in lowercase
flag:ctf{s4v3}
Slow Realization
It gives us a flag.pdf and a jpeg picture
The EOF of jpeg file format is ff d9, so there is actually a mp3 file concated behind this jpeg. It’s OneRepublic - Counting Stars, but there are some morse code and a weird woman voice. The morse code is not the password, which is
.--. .- - .. . -. -.-. . .. ... - .... . -.- . -.-- .--. -.-. - ..-. -. ----- - .... ...-- .-. ...-- |
I thought that the password is inside the vocal between morse code. Tried to apply reverse, invert, or normalize individually on it, but I still can not get a clear version of the woman voice
Luckily, I get the password by dictionary attack…., it turns out to be congratulations, WHAT ?
It really sounds like that after I knew the real password is congratualtions,but it also sounds like slow realization?
Can someone teach me how to get the password in right way?
flag:pctf{y0u_h34rd_m3_r1ght}
Late PR
strings it, done
Is this the intended solution ??
flag:pctf{Late_submissions_can_be_good}
Cryptography
Spoiler
There are some additional information concated after the %%EOF of pdf
%%EOF0000006a0000006f0000006e000000730000006e0000006f000000770000006900000073000000640000007200000061000000670000006f0000006e00000062000000790000006200000069000000720000007400000068 |
It’s a hex string 6a6f6e736e6f776973647261676f6e62796269727468, xor it with another hex string show in pdf.
flag:PCTF{JON_IS_TARGARYEN}
Add them Sneaky Polynomials
We get some polynomials equations:
p = x^406 + x^405 + x^402 + x^399 + x^397 + x^391 + x^390 + x^387 + x^386 + x^378 + x^374 + x^372 + x^371 + x^369 + x^367 + x^364 + x^360 + x^358 + x^357 + x^352 + x^350 + x^345 + x^344 + x^341 + x^336 + x^335 + x^334 + x^333 + x^331 + x^330 + x^329 + x^328 + x^327 + x^324 + x^322 + x^320 + x^314 + x^311 + x^308 + x^307 + x^303 + x^300 + x^299 + x^296 + x^295 + x^290 + x^289 + x^287 + x^279 + x^271 + x^266 + x^264 + x^262 + x^260 + x^257 + x^256 + x^252 + x^249 + x^248 + x^246 + x^243 + x^239 + x^238 + x^236 + x^233 + x^230 + x^227 + x^225 + x^223 + x^222 + x^220 + x^218 + x^216 + x^215 + x^209 + x^208 + x^207 + x^204 + x^202 + x^199 + x^190 + x^189 + x^185 + x^184 + x^180 + x^177 + x^176 + x^175 + x^172 + x^167 + x^166 + x^162 + x^160 + x^159 + x^155 + x^154 + x^149 + x^147 + x^143 + x^137 + x^135 + x^131 + x^129 + x^126 + x^124 + x^122 + x^116 + x^110 + x^108 + x^105 + x^104 + x^100 + x^99 + x^97 + x^94 + x^93 + x^90 + x^88 + x^87 + x^86 + x^85 + x^83 + x^75 + x^73 + x^69 + x^63 + x^62 + x^57 + x^54 + x^51 + x^44 + x^41 + x^38 + x^37 + x^36 + x^34 + x^29 + x^28 + x^26 + x^25 + x^21 + x^20 + x^19 + x^16 + x^15 + x^14 + x^13 + x^6 + x^5 + x^2 |
According to challenge’s description, we can extract a string from these equations
Obviously, if we plug x=2 into equations we can get some “binary strings”.
For example, $2^5+2^4+2^2+2^1+1 = 110111_{2} = 55$, that is the ascii code for 7.
After evaluation, we get some meaningless strings.
But once we xor them together, the flag shows up
flag:pctf{f1n1t3_f13lds_4r3_m0r3_us3ful_th4n_y0u_th1nk}
The Order of the Phoenix
After google the hint Eleven scientists are working on a secret project.......?, it’s a challenge about Shamir’s Secret Sharing. Read the content of QRcode first
1-d301da5536a5d8b8e2be50a7584127eb3704025f048cf72335f1b301b852b30a |
Guess the hexadecimal digits split by - are x and y on the x-y plane, then ….
We have to sovle an equation which derives from these coordinates by Lagrange polynomial. I did’t decrypt it on my own implementation, the problems is that I used the wrong the prime. Using a github repo call secret-sharing to help me.
plain text:pctf{sh4m1r3_w4s_4_gr34t_m4n}\n
flag:pctf{sh4m1r3_w4s_4_gr34t_m4n}
Help Rabin
It’s Rabin cryptosystem, which needs the factor p, q of n to do the decryption. The problem in here is that it generates n by mutiple two primes which are close to each other, this makes us are able to factor n by brute force.
from decimal import * |
Then follow the steps on wiki, we can get the plaintext in one of the 4 decrypted messages:
Hey Rabin, would you like to be the front end to my back end? Here is your flag: pctf{R4b1n_1s_th3_cut3st}
flag:pctf{R4b1n_1s_th3_cut3st}
Easy RSA
It gives some parameter used in RSA
e=217356749319385698521929657544628507680950813122965981036139317973675569442588326220293299168756490163223201593446006249622787212268918299733683908813777695992195006830244088685311059537057855442978678020950265617092637544349098729925492477391076560770615398034890984685084288600014953201593750327846808762513 |
The e is too big so that may cause the d become small enough to satisfy the condition for wiener’s attack
I used featherduster to apply weiner’s attack here and get d successfully
d=12978409760901509356642421072925801006324287746872153539187221529835976408177
The secret message is Here is your flag, pctf{Sup3r_st4nd4rd_W31n3r_4tt4ck}\n
flag:pctf{Sup3r_st4nd4rd_W31n3r_4tt4ck}
Decode This
There is a linear equations :
z = (x*key[0][0] + y*key[0][1])%26 + 97 |
Cuz we know that there must be a pctf in plain text, it’s able to solve this equation. I didn’t get the flag in my first trial, cuz I assume that pctf is the prefix of plaintext. After a while, I realized that crypto challenges of Pragyan always like to give us some xxxxxxx flag: pctf{xxxxxxx}, so , all we need to do here is to brute force the position of pctf in the plaintext.
Solving equation is ez in python, because there are lots of package doing this for us (z3, Sympy, sage … etc).
ram has a little secret for you right here it is pctf i like climbing hills what about you
Miscellaneous
EXORcism
It gives a txt file which contains lots of 1\n and 0\n, it’s a bitmap of an QRcode
Convert it to image by python

The message is 160f15011d1b095339595138535f135613595e1a, a meaningless string
Xor the first 4 char with pctf to check if this was the xor result of flag , then the xor-key turned out to be flag.
flag:pctf{wh4_50_53r1u5?}
Binary
Feed_me
Lazy, use socket and z3 to solve this
flag:pctf{p1zz4_t0pp3d_w1th_p1n34ppl3_s4uc3}
Secret Keeper
Login as admin then it will print flag
Obviously, it has a UAF bug after remove a user. It just clean and free the chunk of account, but not remove the user from the list, we can even login with null usernam and original password.
What’s more, the first registed user’s username can be rewrote as admin
exploit
First, register a user with name whatever and password whateverpassword, then delete it
Next, register another user with name whatever2 and password admin
Cuz this binary malloc for password first, the chunk which second registed user using for password is actually the same chunk of the first user’s username
Now we can login as admin with password whateverpassword to get the flag.
flag:pctf{"ThiS_S3rV1ce-1s$t0T411Y-cR4p_But_w3_34Rn_$$_4nyWaYs"}
Super Secure Vault
The binary ask for key and password.
The key has to satisfy some modular equations :
key % 27644437 == 213 |
We can derive key easily from these equations by CRT (Chinese Remainder Theorem), which is 3087629750608333480917556
If the key passes the verification , binary concats 27644437104591489104652716127 and 08 after the key in the func2. Then it will try to verify password by looking up a hard-coded array , matrix. In summary, it’s trivial, can be done by idapython.
from idaapi import * |
flag:pctf{R3v3rS1Ng_#s_V311_L0t_Of_FuR}
Armoury
Format string vulneralbility, leak the GOT entry and find the correct version of libc.
Then use %n in format string to overwrite the return address to one gadget.
flag:pctf{“W@r_1sN3v3R@_las41nG_s0lut1on#f0R_any_pr0bleM”}